Web3 Anti‑Scam Guide: OSINT, Tokenomics & Smart Contracts
Learn to spot and verify Web3 scams using domain OSINT, tokenomics analysis, and contract checks, with a practical checklist. Includes real‑world examples and a safe‑reply template for suspicious outreach.
Welcome to Hoken Tech.
Scams in the blockchain space no longer come only as “miracle investments”: they often disguise themselves as professional opportunities, collaboration proposals like “fractional CTO,” or developer roles with immediate start.
How a modern Web3 scam thinks
Fraud operations combine three psychological levers: authority, urgency, and simplicity. Authority leverages compliments on your profile and big numbers (“multi‑million budget”); urgency pushes to “talk right now” or “seize the window”; simplicity promises “stable” returns or “risk‑free” onboarding.
The goal is to quickly pull you out of verifiable contexts: private calls, non‑professional chats, token purchases, or signatures from your wallet as a “technical test.”
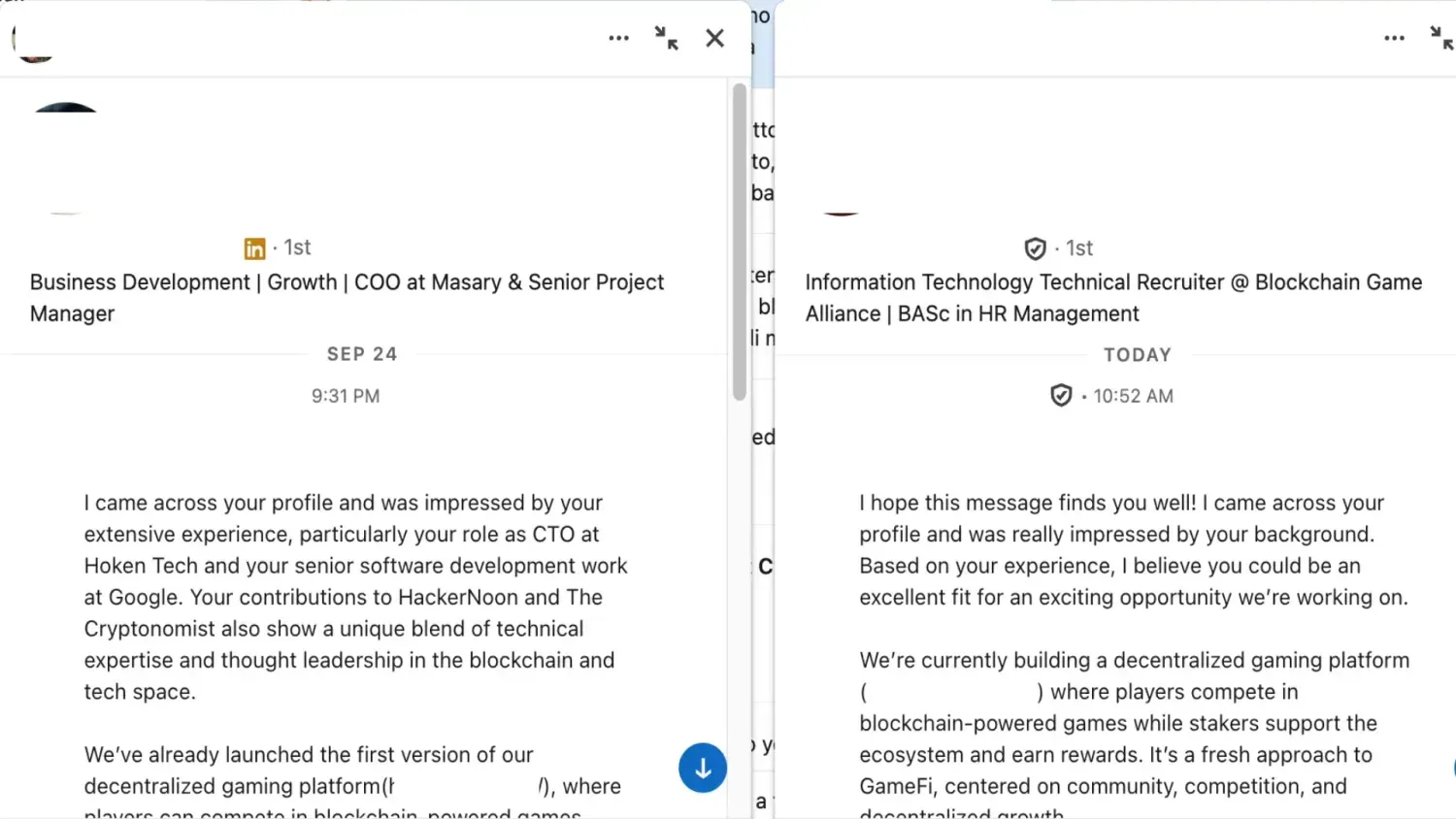
Practical case (anonymized)
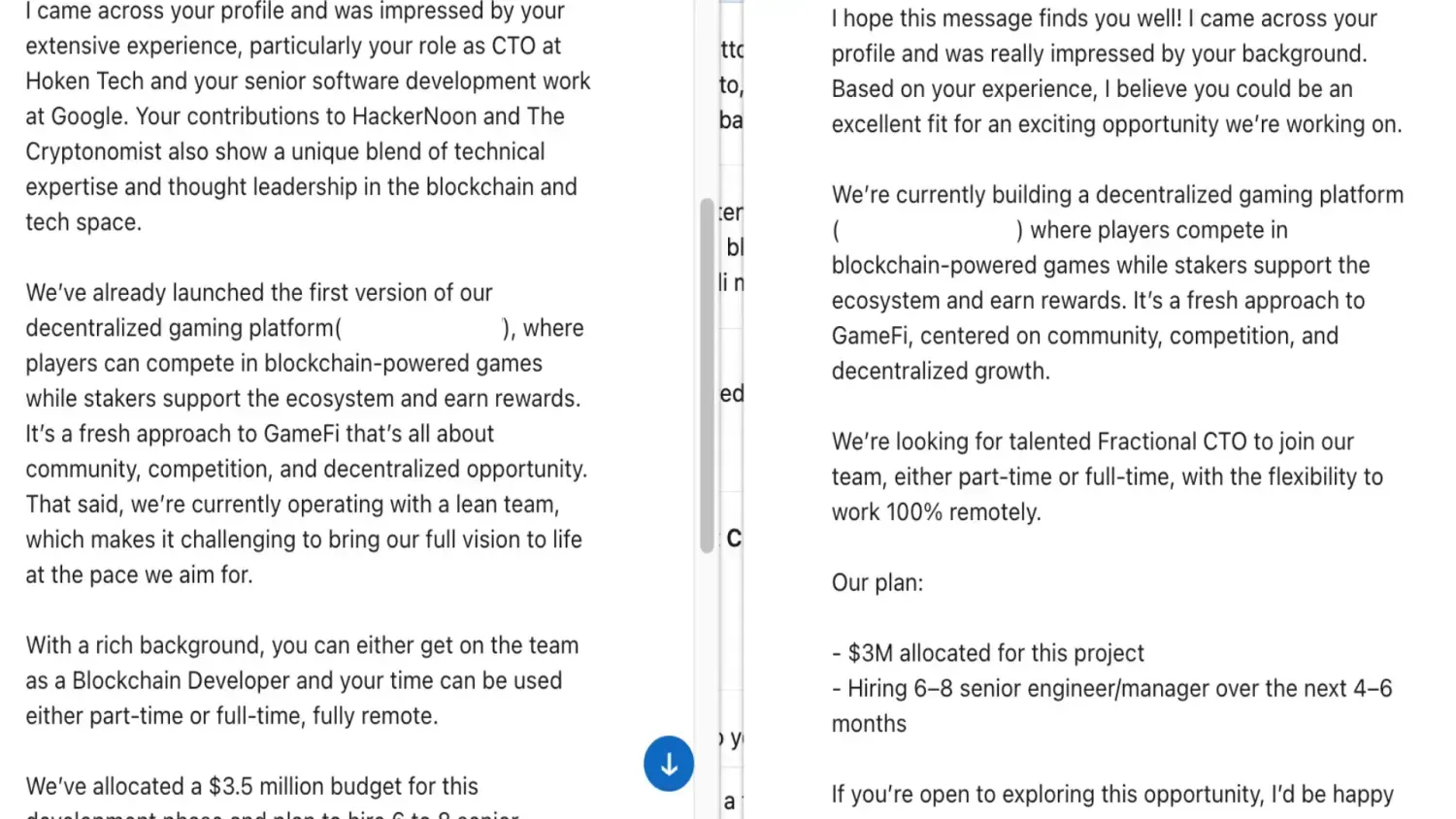
The material shows near‑identical messages: same .io link, same narrative about decentralized gaming, senior/CTO role even part‑time and fully remote. The numbers wobble: in one text the budget is “about 3.5M,” in the other “3M”; hiring is identical (“6–8 seniors in 4–6 months”).
Related documents reveal other typical signs of pyramid schemes: promises of “stable” and “zero‑risk” returns, unlimited referrals, very long fund lock‑ups, and hyper‑inflationary tokenomics. It’s the classic “Ponzi with a Web3 twist”: new entrants fund the rewards, lock‑ups delay withdrawals, marketing keeps the flow going.
Verify identity and company: where to start
Before the technical part, make sure there’s a real counterparty. A serious company provides legal name, jurisdiction, registration number, and uses email on its own domain.
Profiles that avoid official registers, change their story about headquarters and incorporation, or insist on generic mailboxes are a strong red flag. If there are no verifiable documents, do not proceed.
Domain and OSINT traces: what the infrastructure reveals
The domain is often revealing. A freshly registered .io, with fully redacted WHOIS and no history on the Wayback Machine, indicates “disposable” use. TLS certificates visible on crt.sh show timing and CAs; tools like SecurityTrails or DNSlytics help you spot suspicious migrations.
If indexing is minimal and the Legal/Team pages are thin or batch‑created, the likelihood of a façade increases. Practical examples:
whois esempio.io curl -I https://esempio.io
Certificates: https://crt.sh/?q=esempio.io
Technical documentation and code: substance or marketing?
Be wary of generic whitepapers on “super convenient” platforms without independent audits. A healthy project shows active public repositories (commits, issues, contributors), changelogs, tests, and a roadmap that’s being met. Real audits indicate the contract hash, bug severity, and remediations; vague mentions or “audits announced” aren’t sufficient. If you only find glossy PDFs and no technical proof, withhold judgment.
Tokenomics and smart contracts: the checks that matter
Here we move from claims to facts. On Etherscan/BscScan/Polygonscan, verify: verified source code, presence of proxy/upgradeability, timelock, and multi‑sig. Analyze the owner’s permissions (mint, pause, blacklist, variable fee), holder distribution (concentration in top‑10), and the liquidity state (LP lock or burn on known services).
In the examined case, the mix of exaggerated supply, prolonged lock‑up, and “risk‑free” promises is incompatible with a sustainable economy.
Community and reputation: the social thermometer
Channels with big numbers and tiny engagement suggest inflations. Independent communities quickly expose “unlimited” referrals and “stable” returns: look for historical discussions and note if uncomfortable questions are removed. If managers push to move to private chats for “detailed explanations,” that’s a well‑known pattern.
Job offers tied to the token: the strongest signals
Recurring patterns: “copy‑paste” texts from different senders, inconsistent financial figures, very senior roles offered part‑time with total responsibility, and requests to switch to poorly traceable channels. Any request for money, token purchases, or signing transactions from your own wallet as part of the selection process must be refused without exceptions.
Safely responding to a suspicious contact
Keep it polite and firm. Ask for verifiable proof and refuse payments or signatures. A useful text:
“To proceed I need company documentation (legal name, registration, and headquarters), contacts on the corporate domain, links to the independent contract audit, and public repositories. I do not make deposits or sign transactions from my personal wallet for selection processes. If you prefer, send a standard NDA for review.”
Daily operational hygiene
Separate identities and tools: a dedicated email for crypto contacts, a profile with limited visibility of contact details. Use a “sandbox” wallet with no funds for any signature tests and periodically revoke permissions with dedicated services. Adopt a Password Manager and TOTP 2FA; avoid SMS. Keep screenshots, chat exports, and document hashes for possible reports.
Conclusion
The best defense combines business common sense and technical verification. When a job opportunity revolves around deposits, proprietary tokens, or “stable returns,” treat it as a very high‑risk investment and demand verifiable proof.
The case at hand shows the key signals: replicated narrative, inconsistent numbers, unsustainable economy, and a strong push for recruitment. With the above control flow and a bit of operational discipline, you can dismantle most of these attempts before they cause harm.
nft, hoken tech, blockchain, cryptoart, eos, nft art, artificial intelligence, ai, watch authentication, crypto artist, nfts, web3, nft game, web3 game, videogame, nft distributor, videogame blockchain